How Cyber Risk Score ™ Works
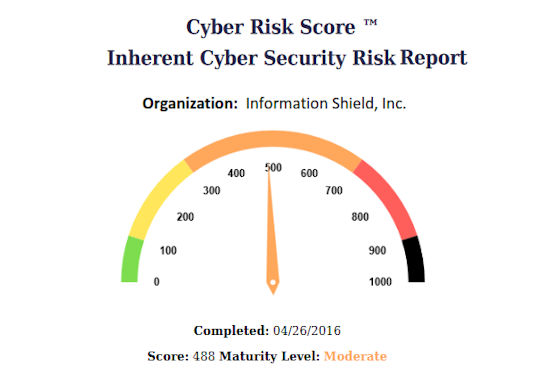
The Cyber Risk Score ™ program assesses your organization in two primary ways. First, we asses your Inherent Risk Score (IHR), which is a measurement of your organization’s cyber risk exposure based on the characteristics of your business. For example, organizations that process a large amount of sensitive personal information (PII) are generally at greater risk than organizations that do not store or process sensitive information.
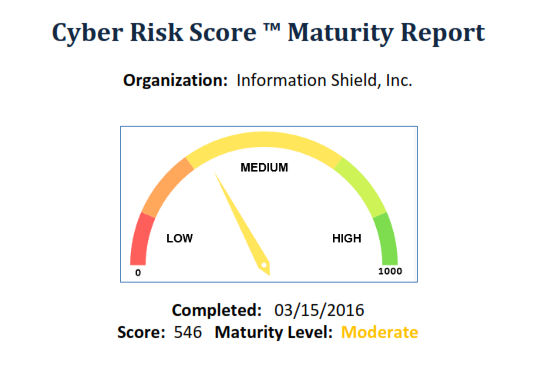
Next, our Cyber Maturity Risk Score is a measurement of your organization’s cyber risk “maturity” based on key information security principles. In this step we assess how well your organization is adopting security “best practices” that have been shown to be effective in protecting information.
Here’s How It Works…
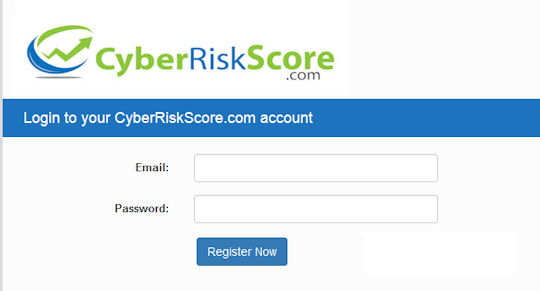
Email address, password, and company name – that’s it, that’s all you need to get started. No credit card number, no “expires in 30 days” trial period. We just want to make sure this site is being used by legitimate businesses and that you have a way to securely access your results anytime you want.
Step 2: COMPLETE THE INHERENT RISK ASSESSMENT
There are two parts to understanding your organization’s level of cyber risk. The first is to mea sure your “inherent risk” – risks that come from the fundamentals of your business – industry, size, structure, and certain technology choices. This part has 9 questions, grouped into 4 categories (for reporting purposes) and should take you about 5 minutes to complete.
sure your “inherent risk” – risks that come from the fundamentals of your business – industry, size, structure, and certain technology choices. This part has 9 questions, grouped into 4 categories (for reporting purposes) and should take you about 5 minutes to complete.
Step 3: COMPLETE THE CYBER RISK MATURITY ASSESSMENT
The second part of measuring your level of cyber risk is to see what you are doing to protect y our data and mitigate your inherent risks. This is by no means a comprehensive audit, but the 21 questions across 5 consolidated Information Security categories covers the fundamentals and will give you a pretty good idea of where you stand.
our data and mitigate your inherent risks. This is by no means a comprehensive audit, but the 21 questions across 5 consolidated Information Security categories covers the fundamentals and will give you a pretty good idea of where you stand.
Step 4: REVIEW YOUR RESULTS
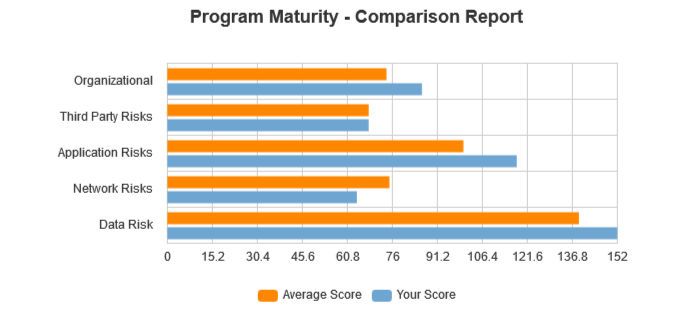
That’s it, you’re done. In about 20 minutes you will have a solid report you can look at online or  download as a PDF. You will get your scores for each type of risk assessment, a break down by category, and how you compare against others. You can even go back and adjust your answers to see how that affects your score or to account for changes in your Cyber Security Program.
download as a PDF. You will get your scores for each type of risk assessment, a break down by category, and how you compare against others. You can even go back and adjust your answers to see how that affects your score or to account for changes in your Cyber Security Program.